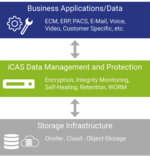
Architecture
iCAS adapts to your IT infrastructure and adds compliance, data integrity protection, and WORM storage (Write Once Read Many) to your existing systems.
After connecting to your business applications, such as DMS or PACS, the data is written from the application to the iCAS fileshare. iCAS combines the metadata with the archived objects in patented CSCs (Content Storage Containers), which are protected against manipulation and unauthorized deletion.
The CSCs are stored as files on the existing IT infrastructure — whether onsite, cloud or object storage. CSCs can be migrated securely, cost-effectively and without loss, even while running business operations.































