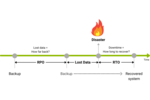
3-2-1-1-0 backup
Because even the backup itself is not immune to data loss, a solid backup strategy is fundamental. One backup copy is not enough. Even the backup can be damaged or destroyed - companies always need more than one copy and must protect them especially.
Why?
If there are multiple copies in different locations, it is much less likely that all backup copies will be lost, corrupted, or encrypted by ransomware at the same time.
The 3-2-1 backup rule is a well-known and simple rule, and still forms the basic framework of a solid backup strategy:
- At least three data copies are to be kept. In addition to the originals of the productive data on the primary storage, the other two data sets serve as backups.
- Data should be stored on at least two different media.
- One backup copy should be kept in an external storage location (offsite or geographically separated location).
The important thing with this strategy is that at least two storage targets are physically separated from each other in case of a fire or natural disaster, for example. Nowadays, this can even be fulfilled within a storage system, such as in a scale-out cluster with asynchronous replication.
For higher protection, two items can be added to the 3-2-1 backup rule: an offline, airgap, or immutable copy and zero errors in the backup process when restoring the data.
Offline means that there is no longer a connection to the infrastructure. If a hacker has access to the infrastructure, all data with online connection can be affected. An offline backup copy means that a hacker no longer has access to it. Such an offline backup is also called an airgap backup.
This category also includes immutable backups, which are protected against changes or deletion thanks to the WORM principle, for example. A common method for this is the use of S3 Object Lock.
The 3-2-1-1-0 strategy goes one step further and requires that backups are stored and restored without errors. There should be zero errors during recovery - backups are too important for this. To achieve this, companies must perform recovery tests at regular intervals and check that everything is working as it should during the recovery process.